FUSION如何实现世界上第一笔分布式签名跨链交易

Table Of Content
FUSION如何实现世界上第一笔分布式签名跨链交易
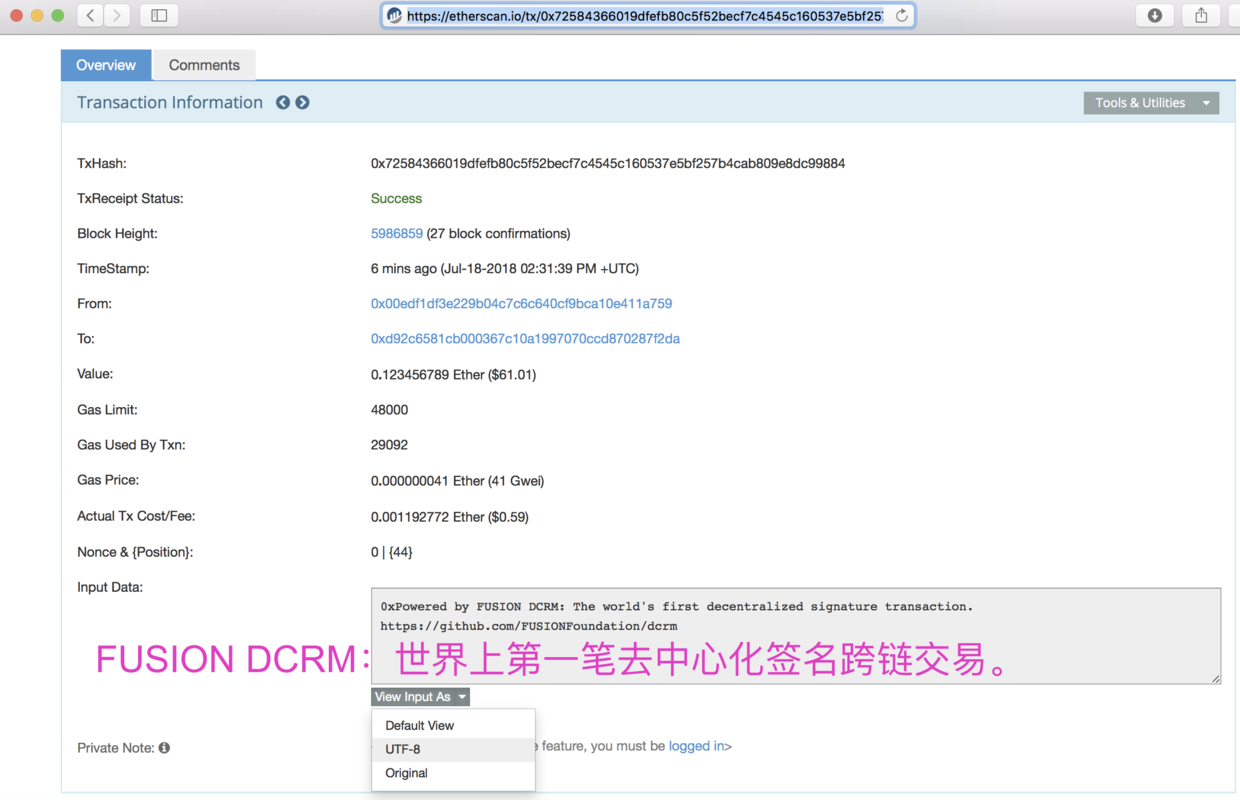
近期FUSION项目宣布通过DCRM技术实现了世界上第一笔分布式签名的跨链交易。
交易地址:https://etherscan.io/tx/0x72584366019dfefb80c5f52becf7c4545c160537e5bf257b4cab809e8dc99884
我们看到这笔交易是在以太坊上的:
块高度:5986859 时间:Jul-18-2018 02:31:39 PM +UTC 转账:0.123456789 Ether 交易数据记录:Powered by FUSION DCRM: The world*'s first decentralized signature transaction. https://github.com/FUSIONFoundation/dcrm*
交易是真实的,但还是会有疑问:这是真的吗?什么是分布式签名交易?和普通交易有什么区别?这笔交易是怎么实现的?为什么说是世界上第一笔分布式签名跨链交易?
1. 什么是分布式签名
FUSION项目实现的DCRM分布式签名技术使得用户可以把拥有的数字资产跨链Lock-in至同一区块链平台,也可以随时跨链Lock-out至指定账户。该技术支持所有和比特币一样加密算法控制的数字资产,包括90%以上的主流加密数字资产:BTC、ETH、USTD和ERC-20 Token等。
分布式签名基于区块链最核⼼的密码相关技术,从最底层密码算法解决跨链去中心化信任问题,综合采用了分布式密钥生成、秘密共享、门限签名、承诺方案、同态加密和零知识证明等密码学算法,这些算法经过证明安全,就像比特币加密算法一样。Lock-in后的数字资产是由FUSION区块链网络分布在全球的成千上万个非中心化节点以分布式密钥算法进行管理,资产账本是公开记录在区块链上并且无法篡改的,用户可以放心的信任开源代码和加密算法。
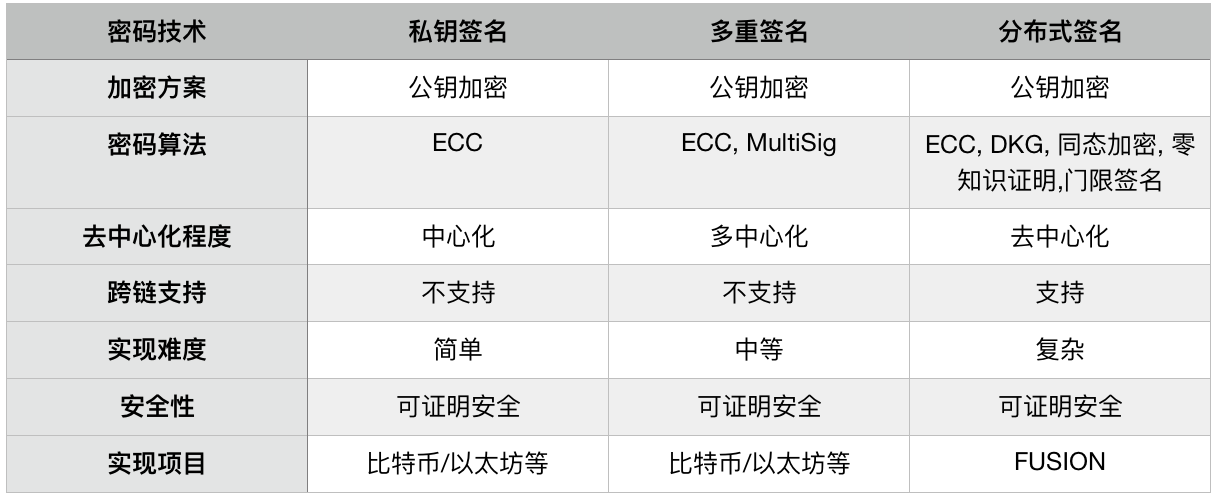
签名技术对比图
不管是比特币还是以太坊,普通交易是由用户通过钱包用私钥进行签名完成,而分布式签名交易则是由区块链网络里去中心化的节点共同签名完成。更详细的信息请参考笔者的另一篇文章:FUSION:DCRM分布式签名技术
2. 这笔交易如何实现
这笔交易是通过FUSION的DCRM技术实现的,代码位于FUSION项目的github官方地址:https://github.com/FUSIONFoundation/dcrm DCRM程序核心功能是生成分布式私钥和公钥,以及完成分布式签名。
为了完成和以太坊的交易,还需要交易程序,笔者实现的go语言测试代码位于:https://github.com/zhaojun-sh/dcrm-test 交易程序的主要功能是构造一笔交易数据并且发送至以太坊网络。
由于目前DCRM还处于测试阶段,还没有钱包支持分布式签名交易,所以通过上述代码来演示实现流程: A. 生成分布式私钥控制的DCRM地址 运行DCRM的代码得到如下结果,这代表着4个节点分布式生成了4个私钥和一个公钥,通过公钥可以生成地址(一台服务器上模拟4个节点)。
--Info: User 0 generate Private Key Share PrivateKey Share: 84985294175903376931445795015467894006937990435985966931354507719444581255012--Info: User 1 generate Private Key Share PrivateKey Share: 84940305801941904466664650218833612629672900930983791755864604768328058215142--Info: User 2 generate Private Key Share PrivateKey Share: 48301921624326365388572144770320542374756243070409113696101196017150962650950--Info: User 3 generate Private Key Share PrivateKey Share: 74476474800750184490014153736266688989328133924980580120573080366704112843538--Info: Calculate the Encrypted Private Key EncPrivateKey: 173329730713759195632158208048813204114677455921675775304258144252371179815430961141231018602754919847223671130038851235770493934212281874570018195132877748444798739739795821227577726293248811650538740502822576453171345141334474759008820338548050683359877810788469256044058927828890465419699614086485143919938663088234744802312667115166497698717611200939616006150333960967798774705098678363760859206718107587099802390681427713171866933375406933443101361557556923318129027997214648941448667715701871121536023557498580309841607312020839799234252343853295268206102175564188138151785998492090757135839568614767948113549479344169054960239235128852314494413754249563707980651899522410043787232916922313334490261299518909453339384085251688068082587884795809168467783742478303912915276925432140041395031792470836030833153327906657603100987211750311974883361669839719389126905701251147103644438573352551485776981716454187236792466740625455113592376164739273665716111784053089429116637141064039346004344920260636335713841450769486173791590749468963530444491755779006306793557058495300565853675068369925243102714680350161348688564986745843917723099482239970825667470784248735260412087349787452160933767617900074467470922767255036695841661683158--Info: Calculate the Public Key PublicKey:(69569e08f0a701b880002b6437bd7ec73248d7487c04afc0698fe1bdcf6184a9,ac288eceaf75478ff73d325447f3791a5c5ef3d8979cb5b6e02bebb9e6802c6,cf3a739c665c0c242ebee6cf7d15aeddd7612934ad91090d0aabb7ec08fae58a,0)
B. 用户手动转账ETH至此地址 新生成的DCRM地址需要用户转账一些ETH至此账户以便测试。
address := common.BytesToAddress(crypto.Keccak256([]byte(PublicKey)[1:])[12:]).Hex()
C. 构造一笔以太坊交易 代码设置好转账金额,接收地址,GAS等。生成交易的RLPHash值,作为分布式签名sign接口的输入。
tx := types.NewTransaction(
0x00, // nonce
toAccDef.Address, // to address
big.NewInt(123456789000000000), // amount
48000, // gasLimit
big.NewInt(41000000000), // gasPrice
[]byte(Powered by FUSION DCRM: The world's first decentralized signature transaction. [https://github.com/FUSIONFoundation/dcrm))](https://github.com/FUSIONFoundation/dcrm`))) // data chainID := big.NewInt(CHAIN_ID)
signer := types.NewEIP155Signer(chainID) fmt.Printf("\nTXRLPhash = %s\n", signer.Hash(tx).String())
D. 基于上述交易的RLPHash值生成分布式签名 DCRM程序基于交易RLP编码后的Hash值生成分布式签名,返回签名结果(r, s, v),程序输出如下:
--Info: User 0 calculate Commitment in round ONE--Info: User 1 calculate Commitment in round ONE--Info: User 2 calculate Commitment in round ONE--Info: User 3 calculate Commitment in round ONE--Info: User 0 calculate Zero-Knowledge in round TWO--Info: User 1 calculate Zero-Knowledge in round TWO--Info: User 2 calculate Zero-Knowledge in round TWO--Info: User 3 calculate Zero-Knowledge in round TWO--Info: Calculate the Encrypted Inner-Data u u: 167882359539886460048672619095828037061329111643251414745211676555428948869232440666993336977554455944749312838261828269611379656662747270604335155510053737439694060600175435654617636403570309241082173612461012385412871482000968630329958949747092238963343539553972464230870111689727913939449238726449418403624095461570530731215530389374555841571129241692283069383096529494928462050236524655282283479738815745614056876328008527820339125620700724624295715039619903333868218155414893965716176564083809246867219944012760926266318004479811080636392068335287726957388592780877629676856719834808475838730841766110186047441502561711792459932145160777456548648462898370195989630954234978571371738985874822299588167695819261041508809865700472042096436851414380083964739632606368746160280493610841023504556898359908030182848043200363247450190212548224843198166212889465101734451385712493515867912739500885843691192416531433016410863483024184820255204692445426438925971829336332531506448000443974817920771646138893722435351052784089752197408232159855783922480181236131999029818676956056127785614058713557924713028456600255438479426572676251661606059111273440879922793674450519127333020764139110858182639803194122265515956079210346616503357996922--Info: Calculate the Encrypted Inner-Data v v: 43465092970691280177698029052618202245685056078947565258101642474160140120330407540175248109690298751814275288454451703773305398185741509852185753150306215984026194016795048194292317711716498211056640649812712851811583007983934212925522905825230004432919497004800896478391331349601388652338760855963317479893596047986417467512421107413879236844183678061499306134562947874452838302811993238059650516185893382623169866263586880164875796032537251995404050449676952957522230734182562856668281738120905795883140513149233553121946217324114869450657562640649071494968909608872146784625143501512145250847930664801143415684445192237834850321262634109554786191930174373507528166033406771214738179630188278351066612645106813192221127592374072217685221726914676421786289281702308836886410623077704304522860395353949085231176541619841708178598143120275005207320150415983577863011613509160587541722536363196385474690882347244294109285484239898306425471091538772546854713952181335787575480882625984694267881042494174010792578406096295045583314468029897776242938665057266633595931199265482356492137672931651515904604223498371308263284434895375425787587483487242768548342536093049416490701618826030117126617905118358594260198292678629414498346977607--Info: User 0 calculate Commitment in round THREE--Info: User 1 calculate Commitment in round THREE--Info: User 2 calculate Commitment in round THREE--Info: User 3 calculate Commitment in round THREE--Info: User 0 calculate Zero-Knowledge in round FOUR--Info: User 1 calculate Zero-Knowledge in round FOUR--Info: User 2 calculate Zero-Knowledge in round FOUR--Info: User 3 calculate Zero-Knowledge in round FOUR--Info: Calculate the Encrypted Inner-Data w w: 83591876179609340873284393652413787577577167385447697152280364830516779412455088062430761227327283437259436387545074973844930547615611299109190377905543063958627565061651648250749587460210544598115956580268139947669635934075861271746001310600688324767190444375813148912090836014443738013857915976485223368672559743127070788514735925763668141504958086921799969022899004948710278687797175451724780989955076012470449632980491259906269114678140596441717658184589490890327625841500912897878583581040590938340628018072475093196174438980348397122367115476691030480215429360943866482635921531318482228793190377125439768391249529511786123141798917101097679523311041632438281496991251745875755447150403039292069095002136343754428656340296166126548132344165211793798353374110488748694821584516513694683099062644952278575639611473134033919580998156082572307230433000457538426766787372044884086413551545050461141965194342408022557722658456921045064021802921500506055772163605132866276649315316478224428858277242890544963276346429078702709179841885083155300789764508519788457669265733403331033732365753561162022458795715460332097719193106353949250850520889967461271664966101030769199155060788492462427503919048384499601064062134834083423512259217--Info: Calculate the Encrypted Inner-Data R R: (84379c5b1d0d1fd295ddc42e5853d120c4e81f6b874ecec87d475a61a7b167bf,bdac131359a69dfd613c80a561244d58ab79d03b9159a390d4e012ffa14b4f89,a62229e25ad7ff2651d2191cf219cd29304f59c5808e5f8d340c85362c348ca2,0)--Info: Calculate the ECDSA Signature in round FIVE Real DCRM ECDSA Signature is (r,s,v): (3647f23d3a6d8407862336e8536dcb8276facf7c5a69749b44dc65d2e467c2fe,64894b2469992357e3dbfcdc64ab5c31983a97531dbdb5a54787f49cb777ecb6,1)
获得分布式签名结果后在交易程序中生成完整交易数据结构RawTransaction。
*//附加签名结果至交易数据结构*
message, merr := hex.DecodeString(signature)
if merr != nil {
fmt.Println("Decode signature error:")
panic(merr)
}
sigTx, signErr := tx.WithSignature(signer, message)
if signErr != nil {
fmt.Println("signer with signature error:")
panic(signErr)
} *//恢复公钥*
recoverpkey, perr := crypto.Ecrecover(signer.Hash(tx).Bytes(), message)
if perr != nil {
fmt.Println("recover signature error:")
panic(perr)
}
fmt.Printf("\nrecover publickey = %s\n", hex.EncodeToString(recoverpkey)) *//恢复地址*
recoveraddress := common.BytesToAddress(crypto.Keccak256(recoverpkey[1:])[12:]).Hex()
fmt.Printf("\nrecover address = %s\n", recoveraddress) *//生成完成交易数据结构RawTransaction*
txdata, txerr := rlp.EncodeToBytes(sigTx)
if txerr != nil {
panic(txerr)
}
fmt.Printf("\nRawTransaction = %+v\n\n", common.ToHex(txdata))
E. 发送交易至以太坊网络 生成完成的分布式签名交易数据后,通过以太坊geth的JSON-RPC接口发送至以太坊网络,由矿工进行打包交易,交易发送成功后会返回交易的hashID供查询交易状态。
*// 本地运行geth连接ethereum网络发送交易: ./geth --rpc console*
client, err := ethclient.Dial("http://127.0.0.1:8545") *// 8545=geth RPC port*
if err != nil {
fmt.Println("client connection error:")
panic(err)
}
fmt.Println("\nHTTP-RPC client connected")
fmt.Println() *//发送交易到网络*
ctx := context.Background()
txErr := client.SendTransaction(ctx, sigTx)
if txErr != nil {
fmt.Println("send tx error:")
panic(txErr)
}
fmt.Printf("send success tx.hash = %s\n", sigTx.Hash().String())
至此完成了一笔分布式签名交易,目前所有DCRM代码开源在github平台上,开发者可以随时测试或审查,FUSION应该非常欢迎开发者提交反馈和更新。最后建议开发者设置chainID=4在测试网络上进行分布式签名交易测试,避免不熟悉交易代码导致账户资金损失。
3. 为什么说是第一笔
FUSION的DCRM分布式签名技术继承比特币以加密算法解决去中心化信任问题的思路,基于最核心的密码算法,通过DKG技术生成分布式私钥,通过commitment算法防止恶意攻击,通过同态加密实现密文处理,通过零知识证明实现隐私验证,通过门限签名实现节点冗余,最终实现去中心化的分布式签名算法。该技术超越了目前常用的私钥签名和多重签名等技术,具有一定的创新性,FUSION基金会已经申请了PCT国际专利。
未来
完成了第一笔去中心化分布式签名交易意味着FUSION的DCRM技术实现了核心技术上的突破,但是这仅仅是个开始,未来FUSION主网上线后,DCRM将要在全世界成千上万个网络节点上迎接挑战形成共识,DCRM将链接所有区块链网络,迎接未来的价值互联网!